
Upgrade Your Drupal Skills
We trained 1,000+ Drupal Developers over the last decade.
See Advanced Courses NAH, I know EnoughStorage and security of health data in the cloud
The ecosystem health is vast, diverse and highly complex, dealing with a large and variable amount of data leads to challenges in terms of storage and security. Cloud computing (CC) has emerged as a response to this challenge, allowing access to data anywhere and on any platform, thus introducing computational gains, especially scalability, agility, and elasticity.
Cloud computing allows doctors, patients and even hospitals, to share data and cross reference information from different diseases and treatments anytime and anywhere, as long as there is an Internet connection. Thus providing opportunities to improve health services from the management, technological, safety and legal perspective. Known examples in healthcare are Microsoft Health Vault, Dossia, World Medical Card and Google Health platform (canceled in 2011).
Currently, the most common cloud computing services can be divided into 3 different models, according to the services they offer:
- Infrastructure as a Service (IaaS): this layer provides networking, computing resources;
- Platform as a Service (PaaS): allows hosting and the implementation of hardware and software to use in applications;
- Software as a Service (SaaS): provides software and does not need to acquire licenses (but the user pays as a "service").
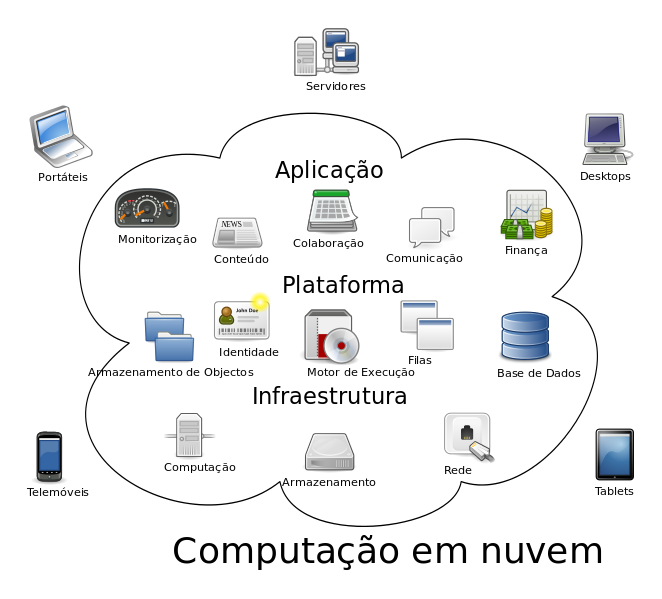
Image from: Wikipedia
Structural models of cloud computing refers to the delivery of CC models for the users, which can be public, private or hybrid.
- In public clouds, applications, storage, and other resources are made available to the general public. Regardless of the service being free or paid, they are similar for all users, each of which can have an instance of this service.
- Private clouds are developed exclusively for an organization, having as main characteristic the individuality of use. Of the three types, a private cloud is the most expensive, because it requires technical and specialized hardware, usually from behind corporate firewalls, and can be acquired and managed by the organization itself or by third parties.
- The hybrid model is a mix of public and private clouds. This type of cloud offers customers greater control and security, and also facilitates the reduction of the service according to demand.
However, all models have advantages and disadvantages – below we present a summary of the various models.
MISSING TABLE
Threats
The Cloud Security Alliance published, in 2010, the main threats associated with cloud computing: abuse and nefarious use of the cloud; unsafe programming interfaces; malicious insiders; shared technology vulnerabilities; data loss; account theft; risk of unknown safety profile.
Abuse and nefarious use of the cloud is when hackers take advantage of questions, such as free trials, to access and use the technology for criminal activities, utilizing resources from the cloud along the way. An unsafe programming interface can expose users to risks, which may lead to data theft. Malicious insiders generally take advantage of flaws in the authorization levels to access information. The vulnerability is associated with shared technologies in cloud programming. Data loss is related to the risk of data being erased accidentally or the existence of a problem in the physical servers without any user data backup. Account theft is characterized by a hacker/attacker that unlawfully seizes access to a specific server in the cloud. The unknown safety profile is characterized by the loss or incorrect migration of a client’s vital security procedure at the time of migration of services/data to the cloud.
Cloud security and privacy
The health information and data are confidential and may have a major impact on people’s lives, therefore, some questions about the use of genetic markers in recruitment decisions have been raised.
Thus, in order to prevent threats, providers of cloud services should have policies, principles (Cloud Governance) and security and privacy mechanisms. To assure this, the cloud computing systems should follow the ISO 7498-2 standard, PCI DSS Level1 certification, SAS70 Type II, ISO 27001, as well as one of the most important protocols to ensure transparency within the cloud – the SLA (service-level agreement).The use of HTTPS in conjunction with WS-security should be the bare minimum when data is accessed using the cloud.
Mechanisms that maintain data security, such as identification and authentication, authorization, confidentiality and integrity, should also be considered.
Each professional, whether doctor, nurse, or service provider must have an identification code or a number to access the information stored in the cloud, so that patient data privacy is guaranteed.
Authorization is achieved using roles on process flows within the cloud, in order to set privileges, and is very important to ensure integrity. Confidentiality ensures control over the organizations’ information that is distributed in different databases.
Integrity refers to the accuracy and consistency of stored data. ACID (atomicity, consistency, isolation and durability) are cloud properties that should be imposed. This feature is achieved by digital signature. Non-repudiation is achieved through security protocols and the use of tokens, key or card for data transmission within the cloud applications, such as digital signatures, timestamps and receipt confirmation services.
Availability relates to the guarantees that the service provider can give the customer that the system will work when needed, without failure or access problems, and with the resources requested by the client. However, one must consider that external problems may occur, for example, with internet access, which can be totally unpredictable.
Below is a presentation of the intersection of service implementation and cloud models compared to the 6 safety requirements, where a check mark (√) means a mandatory requirement in the specific service model and in the underlying implementation model, while an asterisk (*) means optional.
MISSING TABLE
Benefits and challenges
A survey developed by the International Data Corporation (IDC), during the third quarter of 2009, identified the following as the main benefits of using the cloud: payment of what is used only, fast/easy implementation for end users, encourages the use of standard systems, simple system sharing with partners. In terms of challenges, security, availability and performance were the major concerns raised.
Issues not mentioned in the survey, but vitally important, are the legal and audit regulations associated with the cloud, such as physical location of the data, and a transparent data generation for the client and the law. Each country has its own legislation concerning data and procedures. For example, EU rules are substantially more restrictive compared to other countries (particularly the United States). In Europe, Directive 95/46/EC protects individuals with regard to the processing of personal data and the free circulation of such data.
About Drupal Sun
Drupal Sun is an Evolving Web project. It allows you to:
- Do full-text search on all the articles in Drupal Planet (thanks to Apache Solr)
- Facet based on tags, author, or feed
- Flip through articles quickly (with j/k or arrow keys) to find what you're interested in
- View the entire article text inline, or in the context of the site where it was created
See the blog post at Evolving Web

